Hacked & Defaced
My TransMY site was hacked and defaced today, thanks to a Turkish coward. I was pretty surprised of how it can happen when the CMS that I was using (Joomla) was supposed to be quite robust in dealing with security compromise like this.
I was wrong to conclude that Joomla was littered with exploits and backdoors in it’s coding that has resulted to this attack when I was enlightened by the official Joomla forum that announces a possible compromise that was caused by 3rd party add-ons. In my case, my site was pretty much composed of these enhancements without me realising the 3rd party coders doesn’t actually come ‘clean’ in doing their job in contributing to the popularity of the CMS, which was a total shame to the coders/IT community.
On that fateful day I was alerted by an SMS from my brother, who is the co-founder of the site telling me that our site has been defaced. Much to my dismay, I woke up and hurried to my monitor where I left it on overnight for PC spring cleaning. Luckily, I left the site active on the browser where it auto refreshed, so there I was witnessing live for the first time in my entire life of web mastering, my own maintained site was defaced with all it’s ‘glory’.
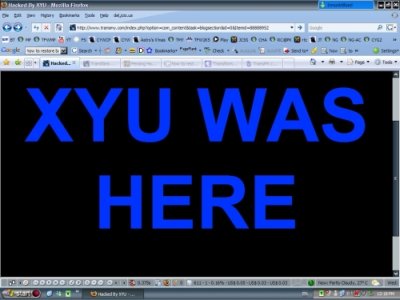
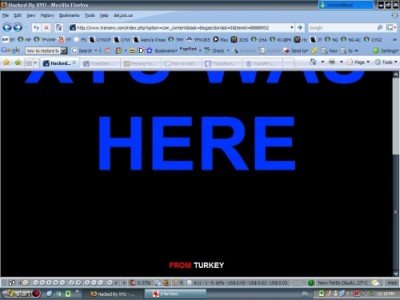
So the tuffie’s name is XYU and he thinks we got problem with viewing fonts.
The add-on that was flawed in my site was the com_expose (ironically its name itself is self-evident) which was meant to be a gallery site. It works fine as a gallery until the hack happen when someone (maybe the coder himself) deliberately compiled the add-on with questionable security loopholes for irresponsible intention.
This come to light when that loophole was eventually penetrated and the hacker managed to upload an index.php file which contain notes above. Being a first timer handling defacement like these, I couldn’t deny how much I panicked. I managed to keep cool eventually by taking a print screen of the attack instead of shutting them down frantically. Then cautiously I FTP-ed my webhost and downloaded the copy of that defaced page. I deleted the original one in the webhost and the site immediately resume as usual. I check almost thoroughly suspected ‘rogue’ files that might have been uploaded. Since the directory was pretty extensive, I abandon the search half way.
I then turned to the official forum for some clues. Eventually, it leads me to this section; http://forum.joomla.org/index.php/topic,192172.30.html . I gave my best bet by believing the security compromise was originaled from com_expose. It was indeed true when I discovered rogue files that happens to ‘appear’ in there all of the sudden. Those files does not belong to the original package (add-on). I download them and deleted the copies.
Being worried of re-occuring attacks, I unloaded com_expose totally. Managed to backup my albums, and upload them elsewhere in a free site such as Flickr.
The next step was summoning all my site Moderators to change their passwords. And in less than 6 hours, all Mods answered the call by doing what was ordered and the site’s routine was restored totally in its original state.
An email fired up to tech-support but didn’t get much help because the attack does not temper their clients accounts, but only mine.
Anyway, the lessons I learnt during this attack;
- Study your add-on carefully before loading them. See the feedbacks and ratings
- Print screen the attack; save them as image files for references
- FTP to your site – copy the file on your local HD for investigation. Delete the original in your webhost.
- Go thorough if you can to spot rogue files. Repeat Step 3 if detected.
- Uninstall the file, module or add-on that you have installed. Delete them clean from your webhost leaving no traces of orphaned files.
- Check your FTP read/write permissions.
- Check your visitation log.
- Change your password immediately; both profile and database details. That applies to your guests authors, co-authors or moderators of your site as well.
- Inform your tech-support. Fired up an email explaining the attack.
- Get help from the help forum where your site platform runs.